Blockchain Security Ecosystem Review In 2021, the World Lost Over $ 9.8 Billion
2021 is a year of ups and downs for the blockchain industry, but blockchain has achieved remarkable results through its distribution, openness and transparency and efforts on internal and external business development. At the same time, after DeFi, the outrage of users around the world and the advent of NFTs and Metaverse took blockchain to an unprecedented level. What is this year? This article will introduce you, starting with the changing nature of the blockchain industry and security concerns.
Blockchain Ecosystem Security Issues
Rules, compliance and oversight
Meanwhile, in terms of housing, the government is reinforcing the importance of the development and implementation of blockchain technology, and the Ministry of Industry and Information Technology stressed that the program has a capacity blockchain and other entities will be improved by 2025. The government will strengthen oversight. In September, several departments published a "Report on the prevention and operation of hypermarket security in financial markets", as well as the National Development and Reform Commission and other bodies shared under the title "Opinion virtual financial management »Mines« Operation ». According to relevant data, the information policy for blockchain-related content was announced in the country in 2021, including school research, technical training, technology design, intellectual property rights, digital agriculture , transport and logistics, protection of transmission and communications. is secure. , health services, digital culture company, etc.
From the perspective of the foreign environment, the governments of many countries continued to pay close attention to cryptocurrencies, the supervision of cryptocurrencies gradually improved, and policies were gradually liberalized. The Financial Action Task Force of the International Monetary Fund's Money Laundering Agency has announced the latest guidelines for cryptocurrencies. El Salvador's legitimate competition, the Ukrainian parliament passed the virtual heritage bill and more.
As we can see,Governments around the world are paying more attention to blockchain, and as an important part of "innovation" blockchain is supported by key organizations.
technology, applications, industry
our country"Blockchain industry"It is also constantly evolving, and many amphibious practices continue to occur. China's first blockchain heritage protection office was designed and established, and Guangdong province announced the country's first patent protection certificate. Huawei announced the patent of the "security chip and process algorithm", Tencent Cloud blockchain is launching our products, and Baidu has implemented a new version of the announcement "blockchain system upgrade method , apparatus, equipment and storage medium ". The China Mobile Metaspace Industry and Communication Coalition committee has been established, blockchain patent applications in China are the largest in the world, accounting for 63%, and the Ministry of Commerce supports the implementation standards New technologies such as blockchain .
Year 2021,Blockchain-based technologyAn important step has been taken. V Dieu et al. instructed EIP-4488 to reduce the fuel consumption of Ethereum Layer 2 Expansion Solution, and Ethereum Arbitrum Layer 2 Expansion Solution will release a new WASM-based Nitro version. Ethereum has completed the London renovation.
security situation
The release of Blockchain technology is a double-edged sword, classification, anonymity and forgery promote the development of the industry, but cause many blockchain security problems. Theft, drug trafficking and crime are just as common.
According to incomplete data on SlowMist's blockchain hacking data, as of the date of the announcement, 231 blockchain security events have been deployed in the blockchain ecosystem in 2021, with a loss of over 9 , 8 billion dollars.

(Source : hacked.slowmist.io)
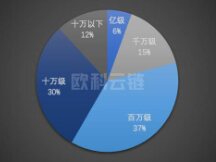
Among them, 170 security incidents, including ecological DApp and DeFi, 15 exchange security incidents, 8 public security incidents, 3 wallet security incidents and 35 other security events occur.

The total loss has increased further since 2018.

Let's identify all the events happening and at the same time provide the weather forecast for each event. This sentence is just a little ice cream, but it is very representative.
Security situations and assumptions
public channel
BSV was affected at 51%.
As of August 4, BSV was thought to have 51% strength and nearly 100 blocks have been rebuilt.
Main network ETC forked tau.
On September 4, Ethereum Classic (ETC) tweeted that the ETC mainnet had been forked due to a malfunction of the Ethereum Geth client.
Solana's mainnet beta will be denied service shutdown.
On September 14, the beta of the mainnet of the public broadcaster Solana began to become unstable at 7:52 p.m. Beijing time, Solana declared bankruptcy on September 21. All operations resumed within 24 hours. The cause of the network malfunction is the denial of service shutdown. At 12:00 UTC, Grape Protocol launched the Raydium IDO, and the robotics industry crowded the network. These changes cause memory to overheat, resulting in greater recognition of faults, causing the network to slow down and possibly shut down.
slow cloudy view
Public chain security vulnerabilities cause small losses, but have a major impact on the entire chain ecosystem. Therefore, public channels must pass a security check before connecting. It is recommended that the public chain team work with the team confidently and securely to implement safety recommendations based on local principles to minimize the risks of creating safety issues and ensure the security of the entire public channel.
cash
Cryptopia hacked dua
On February 20, the New Zealand exchange Cryptopia was hacked again and an investigation revealed that the hacker had access to a wallet that had been there since the period of the hack in January 2019. The wallet is owned by Stakenet and owned by Grant. Thornton, Cryptopia's liquidator. According to the research results, the dormant wallet holds around $ 1.96 million (roughly 1.2 billion earnings) at Xtake, Stakenet's iconic brand.
Wallet in liquid gold against
On August 19, the Japanese cryptocurrency trading platform Liquid claimed that Gold Bag had been attacked. The SlowMist AML team used MistTrack to prevent money laundering to identify and count the total loss of approximately $ 91.35 million (to date). There are over 70 tokens, including tokens, TRX tokens, TRC20 tokens, XRP, etc. and the income has increased.
slow cloudy view
The issue of trade security has become a major concern for trade and consumers, and has become the key to the survival of trade. In particular, in the fourth quarter of this year, various exchanges struggled one after another causing a huge loss.
The exchange was frequently questioned for the following reasons:(1) Exchanges have raised a lot of money and have always been a target for hackers.(2) In general, exchanges are easy to protect, easy to secure and easy to access for hackers.(3) Users do not have sufficient security knowledge.(4) Internal offenses.
For exchanges, it is recommended that major exchanges improve their internal governance and technological processes, and provide security ratings, zero reliability, and cold and hot security tools to improve the security of digital assets. At the same time, actively accept the leader. Users need to strengthen their security awareness, not divulge their personal keys to anyone and at the same time find a platform to prevent phishing incidents.
wallet
Ledger wallets can leak multiple times.
On June 18, Bitcoin hardware wallet provider Ledger warned users that several new scams have recently occurred using fake ledger hardware wallets to buy customers for the use of assets. Package contains forged letter and Ledger hardware wallet. Ledger said that the statement "You must replace your old hardware wallet to protect your money" is a scam and that Ledger Nano money is also bogus. If the user follows the script's instructions and concludes the deal, the user's encrypted device will be stolen.
Several Chivo wallets were stolen
Cibo Wallet is a national digital wallet announced by the government of El Salvador on September 7 to regulate Bitcoin. . With this measure, El Salvador's legal portfolio exceeds 2 million in just one month. However, between October 9 and 14, Cristosal, a human rights group based in El Salvador, received 755 alerts from Salvadorans warning of the theft of Chivo wallets. .
slow cloudy view
Although less than this year includes the wallets themselves, the theft of the fake wallet app withdrawal is amazing. as the voice slows downAccording to a November report, tens of thousands of counterfeit wallets were stolen, resulting in a loss of up to $ 1.3 billion. Establishing security awareness and knowledge of how best to protect your assets can really help. First, find the official site and don't click on any link which is not the official site, second, flip your wallet and keep your correct mnemonic key. In the end, always a surprise, no free lunch. World.
DApplications, DeFi, NFT, Hla-Chain
(1) ETH ecosystem
SushiSwap strikes again
On January 27, SushiSwap attacked again and lost 81 ETH. This attack is similar to the first SushiSwap attack in which it generates profit by controlling the exchange rate of a trading partner. This strike took advantage of the fact that DIGG itself was not trading on WETH, so the attacker formed this trading partner and controlled the start-up price, resulting in a large loss in the exchange rate process. Supporters of his case have worked to make the actual transcript of this statement available online.
$ 12.15 million returned after SIL theft
As of March 19, DeFi Financial Services' SIL.Finance contract was at high risk. SIL.Finance subsequently published an article stating that the incident was caused by the malfunction of the smart license agreement, which affected the overall business plan to deliver commercial products for profit. After seeing that the smart contract could not be canceled due to unreliability, it was able to return to $ 12.15 million after 36 hours of trying like SlowMist.
(2) BSC Ecology
Vulnerabilities and complex strategies
On September 30, the unsecured compound loan process confirmed via Twitter that the COMP tokens were subdivided into differences in the mining process after complying with the deal. Good 62. This has been researched by Compound Labs and members of the community. Compound said its deposits and loans did not appear risky. Compound founder Robert Leshner said that an error in the initial setup of the COMP token distribution value under rule 62 resulted in the distribution of multiple COMP tokens. On October 4, as Compound attempted to correct the flaw, an additional $ 68.8 million in COMP tokens (a total of 202,472 COMP) entered the mining business, which had previously been closed by drip function call. (). .
Our attacks on finance in Crimea
On October 27, Cream Finance, DeFi, went bankrupt and lost approximately $ 130 million. The most commonly stolen funds are Cream LP tokens and other ERC-20 tokens. It would be the third biggest DeFi hacker attack in history. Additionally, Cream Financial has already suffered several loans, losing an additional $ 37.5 million in February and an additional $ 19 million in August.
(3) EOS ecosystem
flash.sx smart link in re-entry attack
As of May 14 at 11:28 UTC, the flash.sx Lightning smart loan agreement was suffering from a "re-entry" default, with approximately 1.2 million EOS and 462,000 USDT stolen. According to legal documents, after the theft of the Lightning EOS Nation loan, the team announced that they had agreed to change hackers' access to the EOS account and send their assets.
The pizza was stolen
At 8 p.m. on December 8, the hacker hacked his spider account using a weak hole to provide an additional certificate to the tripool company on eCurve and the pledge and loan share many tokens in the PIZZA contract. Since then, hackers have created more than 1.3 million accounts and compromised stolen assets. The loss of the PIZZA protocol in this strike is approximately $ 5 million.
(4) polygonal ecology
The SafeDollar algorithmic stability project has been challenged.
On June 28, Polygon's SafeDollar algorithmic stability currency project was reportedly stolen, and it appears that $ 250,000 in USDC and USDT was stolen under unsecured contracts.
PolyYel financial contract used
Income Swap Agreement PolyYeld Financial disputed and provided 4.9 trillion YELD tokens using the contract to sell into the middle class.
(5) HECO Ecology
HSO stole 30,000 HT and fled.
On March 10, HSO, the oracle project of Huobi Eco-Chain HECO, made an IDO and lost 30,000 HT. Subsequently, 24823 HT was recalled after full disclosure by the HECO Star Lab core code team, the HECO tech community, and the HECO White Hat Security Alliance.
XDX Swap has been attacked.
On July 2, the XDX Swap (DDEX) of DDEX, the Hecochain exchange, reached and crossed the turnover of 85.17 ETH (approximately $ 176,000) for Ethereum. Looks like there is a return in the DDEX code. With the support and cooperation of DDEX, Star Labs and HECO White Hat Security Alliance, XDX Swap recovered the money most often involved in this attack, at a total cost of over $ 5 million.
(6) Other ecology
NEAR Ecological Ref.Finance was used due to a contract error.
On August 15, the NEAR Ecological Ref.Finance team discovered bad behavior in the REF-NEAR trading pair around 2 p.m. UTC on August 14 and immediately found an error in the recent contract area. I tweeted that. It has been used by many users and has affected around 1 million REF and 580,000 NEAR.
Solana Ecology Solend has been attacked by hackers.
On August 19, Solend, Solana's green loan deal, tweeted that the contract was challenged by thieves on August 19 at 8:40 p.m. Beijing time. The hijacker also set the APY of the loan at 250%. During this time, the accounts of 5 users were forced to be liquidated. Solend said the strike did not result in money laundering and would result in bigger bugs and better oversight and vigilance in place.
Polkatrain IDO platform Polkatrain yog arbitrage
On April 5, an incident occurred on Polkatrain's IDO platform, Polkatrain. Using PLOT tokens, you collect money and return the money to the user by calling transferFrom in the _update function of the contract. Since the _update function does not set the maximum reimbursement amount of the pool and does not determine whether the total reimbursement amount is total during the recovery period, the bad decision maker can keep calling to swap tokens in order to get a repayment agreement.
Avalanche's chain loan protocol, Vee.Finance, has been hijacked.
On September 20, Avalanche Chain Loan Agreement The Vee.Finance team discovered several anomalous shipments, and upon further investigation, a total of 8,804.7 ETH and 213.93 BTC were stolen (from a total value of over 35 million USD). The bond part is not affected by this strike.
GrimFinance of the Fantom chain was attacked by lightning.
On December 19, GrimFinance, the consolidated revenue of Phantom Chain, was struck by lightning, resulting in a loss of $ 30 million. An attacker uses a function called "beforeDeposit ()" in the GrimFinance vault policy to attack and conclude a malicious contract.
(7) Hla chain system
THORChain, the interconnected process, has been attacked three times.
On June 29, THORChain was attacked with a "false deposit" and lost almost $ 350,000, and on July 16, THORChain was attacked twice with a "false deposit" and lost almost $ 350,000, or about $ 8 million. The loss amounted to nearly $ 8 million.
Cross-Chain Bridge Outdoor Chain Swap affects multiple platforms
On July 11, the ongoing ChainSwap project was fired by hackers, and over 20 project tokens using smart contracts on the bridge were stolen by hackers. The greatest security in DeFi history. According to the chainswap research, the chain exchange bridge quota is automatically increased by the sign node due to a malfunction of the token cross-chain quota code, the purpose of which is to decentralize it further without control. However, uncertainties in the rules have led to the inconvenience that the increase in the number of addresses is not included in the free list. First, on July 2, Chainswap was also stolen and certain user tokens were removed from the wallet associated with Chainswap, resulting in a total loss of US $ 800,000.
Poly Network returns after $ 610 million theft
The poly network attack, which took place on August 10, was the largest security incident in history, with more than $ 610 million in crypto assets stolen in 15 days. The entire blockchain industry and every participant has had its ups and downs with the Poly Network. All related items are now returned to the user, and the function has been successfully restored to its pre-crash level by default.
(8) NWS
Diffusion of NFT scams
On August 2, a scammer called "cryptopunksbot" advertised on Cryptopunk's Discord server, giving NFT clients access to 10 NFT avatars. Stazie, the founder of the NFT project, lost 16 cryptopunks worth at least $ 1 million because she accepted the bogus report. The scammer then sold 5 cryptopunks for 149 ETH ($ 385,000).
slow cloudy view
Since the birth of DeFi, many dangerous things have happened. Many DeFi operations have lost value, doubling, but the piracy situation remains strong. Slow Fog statistics show that DeFi typically has the following vulnerabilities:(1) love at first sight;(2) engagements;(3) compatibility or architecture issues;(4) release a personal key or frontal attack;(5) Violation of the interior and the race.
For team members, a dedicated effort is made to conduct a security screening and in-depth investigation of a project before it goes live in order to eliminate uncertainty and reduce risk. xeeb. At the same time, it is recommended that all actors of the DeFi project present several signatures to strengthen the protection of heritage. On the other hand, since every DeFi project is involved in the process, it is necessary to complete the communication process, and the developer must understand the whole structure of the porting process and the architects design their own plans when porting the code. Other Steps to Avoid Bankruptcy For users, as the blockchain's playing field becomes more and more diverse, users should fully understand the context of the project before investing, to ensure that the project is open and wanted, and be very careful when participating in the project. Be aware of the risks of the project.
other species
pillage
On May 7, the Colonial Pipeline, Korea's largest oil and gas pipeline operator, was forced to shut down due to a planned ransomware attack. . Ransomware attacks interfering with key national processes have caused widespread frustration and concern around the world. In this case, officials from the Department of Justice said they had recovered more than $ 2 million in ransom. However, the US administration has not announced any specific procedure on "how to secure a private key and return the ransom," except that this measure suggested that the United States would respond frequently to blackmail attacks.
fraud
On August 20, the founder of Russia's biggest cryptocurrency scam was shut down for extorting more than $ 1.5 billion from investors. Finiko was created in Kazan in 2019, as a legal entity with the capital of BTC. In December 2020, Finiko announced its own FNK cryptocurrency. According to local data, the developers received BTC from merchants and rewarded them with FNK tokens.
peach
On October 15, Sophos announced in a statement that crypto fraud app CryptoRom stole $ 1.4 million using "supersignature services" and the developer at Apple. To date, Bitcoin addresses associated with scammers have sent over $ 1.39 million, and there may be multiple addresses involved in the scams. According to the report, the majority of victims are iPhone users. According to reports, CryptoRom passes all security checks on the App Store and is still running on a daily basis. The statement also said that Apple "must warn users against the ad hoc distribution or enhancement of applications by configuring applications that are not monitored by Apple."
slow cloudy view
concludes
Although the market value of many cryptocurrencies represented by BTC has been restructured and now the growth of the blockchain market is improving more and more, cryptocurrency breaches are still rampant.According to statistics, the months with the highest security events and losses are April, June and August, from an all ecosystem perspective, Ethereum lost more, over $ 1.3 billion, and BSC Ecology : Attack Fields, Exchanges. and DeFi was further challenged by
For both parties, internal control and technology procedures must be improved, and internal security personnel must ensure that no security-related issues are addressed. The most important and cost effective way is to clarify and understand the security of the project before it is executed to minimize the risk of security issues.
For users, fine-tune the blockchain in a thoughtful way, develop a good idea and a good investment, and improve the risk protection experience. For example, before investing, carefully consider where the smart contract is open, if there is a security assessment of the platform itself and most importantly, keep the mnemonic key private is good and should not be disclosed. to no one.
Finally, we look forward to another year in which the blockchain will explode with more energy, more landing gear, and more productivity.

Scan QR code with WeChat